Securely accessing OT systems from the cloud
One of the challenging issues in the Internet of Things (IoT) is how to securely access on-premises OT systems from remote IT environments. This includes...
- Which personnel can access those OT (Operational Technology) domains?
- Which personnel should have access to specific devices or systems within the OT environment?
- Are these personnel accounts and passwords actively managed to meet information security compliance requirements, such as MFA (Multi-Factor Authentication), regular password changes, and so on?
- Is remote access service normally disabled to comply with the principle of least privilege in information security standards?
- Is the password for the remote access host generated each time it is activated to prevent different personnel from using the same password, thus meeting the uniqueness requirement in information security standards?
- Is there an audit log available for the activities performed by personnel on the host after accessing the environment?
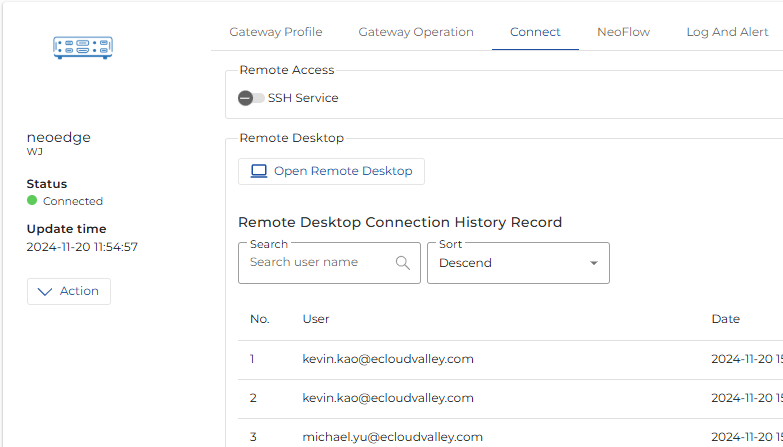
Remote Desktop Service
Subtitle for This Bl
Text for This Block
NeoEdge Central RDP (Remote Desktop Service) provides a secure, simple, and convenient service that allows you to access OT environments from anywhere, offering the ability to access other devices/systems through the desktop on a host within the environment. Key features of NeoEdge Central RDP include:
1. Centralized and unified management of user authentication and permissions.
Administrators can directly use NeoEdge Central's project management, user management, and role management features to plan the permission relationships between personnel and environments, as well as between personnel and devices/systems. For example:
- Using a Multi-Sites architecture to segment different OT environments, ensuring physical isolation of data and transmission.
- Isolating devices/systems within the environment by project, and assigning projects to the required personnel. After logging in, personnel can only access the devices/systems they are authorized to use.
- External vendor accounts are initially set to a closed mode, and are only activated after going through an application process. They are deactivated once the work is completed.
- All accounts are required to enable MFA (Multi-Factor Authentication) to strengthen security measures.
2. No client-side installation is required.
The NeoEdge Central RDP service uses a browser as the user interface, eliminating the need for additional client software installation. This reduces management costs, eliminates the need for software updates, and mitigates the risk of virus infections.
3. Connect to other devices and applications within the environment.
NeoEdge Central RDP requires the deployment of a Gateway host to the OT environment. After users are authenticated and authorized through NeoEdge Central, they can access the following through the Gateway host:
- Open a browser to connect to other devices/applications.
- Open a terminal to connect to other devices via SSH Console.
- Open RDP to connect to other operating systems.
- Open the application software on the Gateway host.
4. Support for the Gateway host.
NeoEdge Central RDP supports:
- X86/64 CPU – Ubuntu 22.04 Desktop OS LTS
- X86/64 CPU – Windows 10/11 OS
- X86/64 CPU – Windows Server 2022
Remote operation footprints and audit logs.
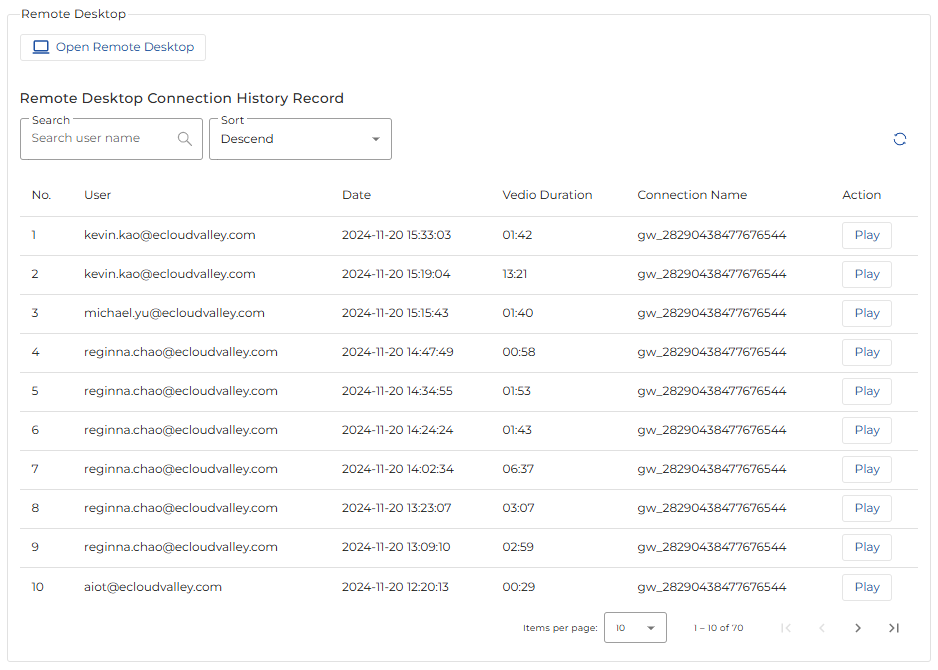
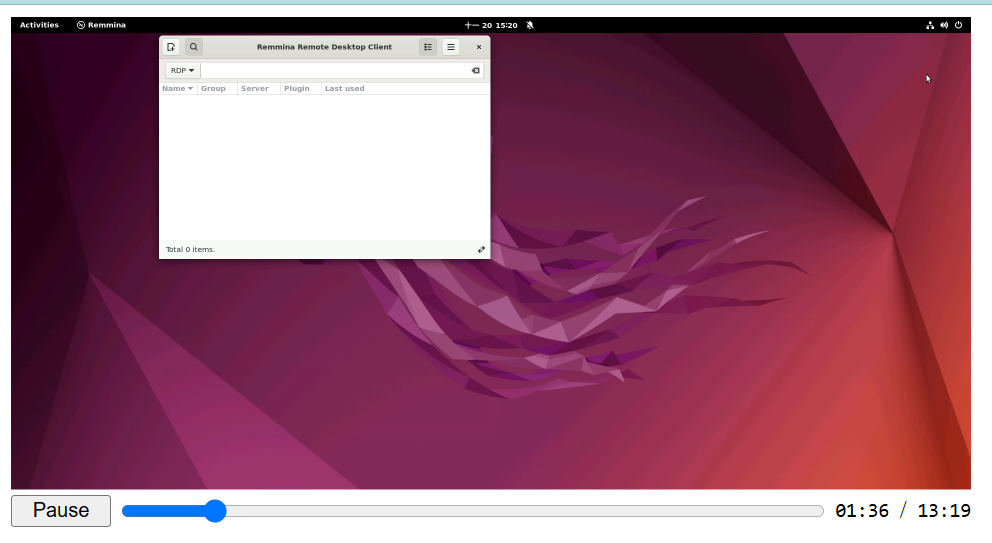
5.1 Screen recording.
Once an authorized user starts the remote desktop service, NeoEdge Central activates the screen recording mechanism, capturing every action the user performs. These recordings are securely stored after being encrypted. Administrators can query, replay, and download these operation logs within NeoEdge Central.
5.2 Audit logs
All important activities performed by users after logging into NeoEdge Central are recorded in the Event Log. Administrators can query and export these activity logs within NeoEdge Central.

